Keith Smith - My Blog
Evernote snoopingWednesday, December 14, 2016 - Posted by Keith A. Smith, in Security
Evernote announced an upcoming change to its privacy policy that would allow company employees to “exercise oversight of machine learning technologies applied to account content” to improve the service.
Evernote’s privacy changes will take effect Jan. 22, 2017 and users are threatening to abandon the service. A few years ago Dropbox also made changes to it's privacy policy to allow it's staff to snoop around in your stuff. The policy changes have to do with machine learning, which Evernote says it is using to “help get you the most out of your Evernote experience.” According to the company’s policy update notice, "Only employees who are fulfilling one of the customer or business needs... will be able to access your data.” Evernote claims a limited number of employees who have undergone background checks will be able to access user data and that users can encrypt notes to prevent employees from reading them. I said it once, and I'll say it again if you upload data, virtual machines, etc. to any cloud provider you essentially have transferred ownership of that data the cloud provider simply allows you to access it. It is imperative that everyone implement encryption and Multi-factor authentication (MFA) also known as (also known as 2FA) where ever possible. I also recommend that everyone use the EULAlyzer to analyze end user license agreements for interesting words and phrases in order to make sense of the nonsensical agreements. -End |
|
 0 Comments 0 CommentsTweet |
|
Windows Update MiniTool is a free alternative to windows updateTuesday, November 1, 2016 - Posted by Keith A. Smith, in MicrosoftWindows Update MiniTool is a free alternative to the standard Windows Update, it puts you in control of updates by allowing you to search, install and block Windows updates as you please. Windows Update MiniTool Will provide the follow options: ◦ Check for updates ◦ Download updates ◦ Installing Updates ◦ Deleting installed updates ◦ Hiding unwanted updates ◦ Get direct links to the *.cab / *.Exe / *.Psf update files ◦ View update history ◦ Configure Automatic Updates This tool is like the external powershell module PSWindowsUpdate, but much more advanced and user-friendly features The tool relies and use same WU infrastructure, all downloading are through WU -- it's not a downloader! I have tested this on server 2016 along with windows 10 and it works great. 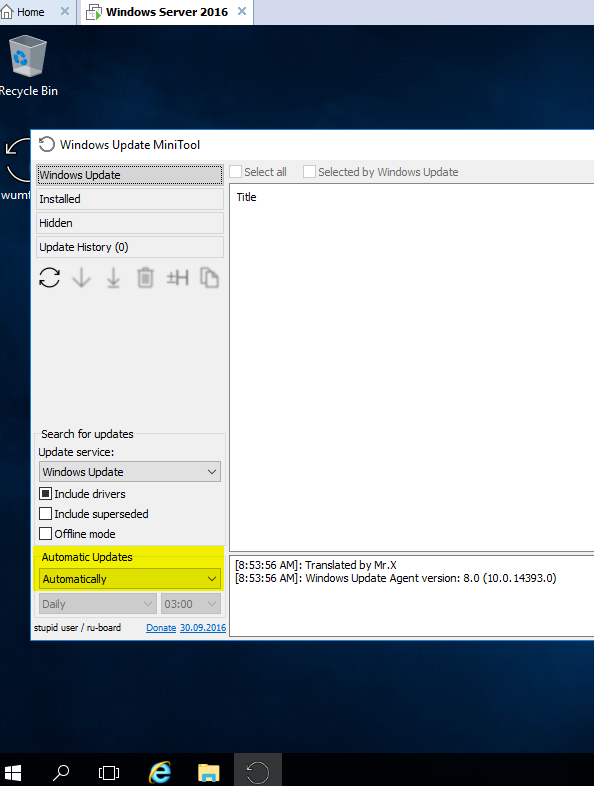 |
|
 0 Comments 0 CommentsTweet |
|
Developing Soft SkillsTuesday, October 25, 2016 - Posted by Keith A. Smith, in Journal of thoughts
Working in information technology is very exciting to me. It is very rare for me to wake up in the morning and not look forward to coming into work. My technical skills that I have acquired through the 14 years I have been in IT has served me well. At the same time though, we all have other skills that are just as important as the technical skills. Lets face facts here, there are always going to be people who know more than me and who have done more than I have. What sets a successful IT person apart from a non-successful one usually comes down to the other skills they bring to the table.
These other skills are called "soft skills". They are key factors in how you react to situations, talk with people, and approach challenges. Believe it or not, these soft skills say a lot about you and have the potential to make or break your career in the end. The real challenge when it comes to developing these soft skills to work in your favor is that they are so tightly entwined with your personality. There are many soft skills to develop, but there are three that I have really focused on through my career. Attitude Attitude is everything in business. If you are an optimist, can see the bright side in a sea of darkness, and can follow projects through with positivity and vigor, you will be valued as an employee. Compare that with the guy who views a project in a negative light and complains about how the project will fail through the process. If you are a business leader, who would you rather work with? Most people would agree they would rather have the guy who is positive and brings them up as opposed to the guy who brings them down. Communication Being positive only helps if you are able to communicate your positivity to the people around you. This counts in not only a verbal sense, but through a written sense as well. Developing this skill requires development in areas like verbal communication, non-verbal communication, and listening skills. This is a soft skill that you develop through the course of your life and career. Teamwork Organizations are looking to become more lean. This means they want cross functional teams that have people who are willing to work with others. If you don't play nice with others, or if you view yourself as someone who works better alone, its time to start developing this soft skill. If you are looking to develop your soft skills, there are many ways to accomplish this goal. The first would be to find a mentor. This can be your boss, a friend, or a leader that you know and respect. We are all more likely to change the way we think and the things we do when we learn from someone who we look up to. The second way is to volunteer your skills to areas outside of your workplace. Take up a cause such as volunteering at a food bank or other non-profit. There are not only soft skill learning opportunities at these non-profits. -End
|
|
 1 Comments 1 CommentsTweet |
|
Must have GPOs for Windows 10Tuesday, September 27, 2016 - Posted by Keith A. Smith, in MicrosoftI started testing Windows 10 Enterprise in my environment. I know there are a number of new features in Windows 10 that aren't great for domains (PIN codes, Microsoft Accounts, etc.). After digging through all the GPO settings, I decided on the on the following. Once the modification was made and applied to the test machines, I brought in a few non-IT staff for UAT testing of the images. Everything went well, so I decided to share the settings I used in the GPO
And last but not least is setting explorer's default to This PC instead of Quick Access by doing the following: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced Value Name: LaunchTo Type: DWORD Value: 1
|
|
 0 Comments 0 CommentsTweet |
|
How to become a windows sysadminFriday, March 11, 2016 - Posted by Keith A. Smith, in Microsoft· Create two networks/VLANs (desktops and servers) · Install Windows Server (VM or standard hardware if you have it available) GUI Mode. · Install another server, single NIC on the server VLAN · Create your first active directory domain controller. · Create another server but this time make it a core server. Make it a domain controller · Test AD replication via the GUI and cmd. · Create an OU for your workstations; create an OU for your users, and an OU for groups. From now on, any new computer or new user account must go into their respective OU. DO NOT MOVE THE DOMAIN CONTROLLERS FROM THE DOMAIN CONTROLLER OU. · Create subnets in Active Directory Sites and Services to match the IP’s used on the VLANs you created. · Check out DNS. Do you have a reverse look up zone? No? Then set it up. · Check out DNS. Records can get old and out of date and will screw up name to IP resolution. Make it so that scavenging happens automatically. · You need to block facebook.com via windows DNS. Make it so that when a DNS look up is performed, computers use a loop back address. Test this via cmd to make sure it resolves as expected. · Set up DHCP on the first domain controller. · Set up a scope to hand out IPs for the Desktop VLAN. Make it so that this DHCP scope will be able to give endpoints the information they need networking wise to join a domain · Install a Windows endpoint or newer PC on the desktop VLAN · Your Windows endpoints are not getting IPs. Why? (hint: it's a routing/broadcast/relay issue) · Join that desktop to the domain · Now that you are getting IPs from your DHCP server, configure DHCP clustering. Load balancing or failover is your choice. Now test it. · Create a non-domain admin account in AD. Fill out the whole profile once the account is created. · Login to that Windows endpoint as a regular AD user and an Admin user. Try to install software under the non-admin account first and then the admin account. What is the difference? · Create another non-admin account. Make this non-admin user a local admin on that computer. Who else is also a local admin before you make any changes, · Review the attributes of that account in AD. You will need advanced features for this. · Create an AD group. Add the first non-admin account to this group. · On that desktop, install the RSAT tools so you can remotely manage another computer · Setup remote management on the core server so that it can be managed from the MMC of another computer (there are a number of ways to do this) · Find out what server is holding the FSMO roles via the GUI and the command prompt. · Split the FSMO roles between the servers. Try to keep forest level and domain level roles together. · On one of the domain controllers, create a file share set it so that only administrators and the second non admin account have access to it. Create another folder and give only the AD group you created permissions. · Use group policy to map both shares as network drives as a computer policy to the endpoint. · Login to the endpoint as the first domain user. Do you see the network drive mapped in windows explorer? No? Use gpresult via the cmd to find out why. If you do see it, try to access the drive. You should be denied if you set permissions correctly. Login as the second domain user, they should be able to open the mapped drive. · What if the account in the group tries to access the second drive? You should be able to get in. · Login to the windows endpoint as the second non-admin account. You should not have access to this drive because you are not in the group. Do not log off. Add this account to the group. Can you access the drive now? No? Logoff and login back in. Can you access the drive now? · Remove the share from the domain controller. We don't like putting shares on domain controllers if we don't have to. · Build out another two servers and join it to the domain as member servers. · Install DFS and File server roles/features on both servers. · Create a file share on bother servers with the same folder name. Create files on both servers. Make sure they are different. (i.e server1 will have "TextDoc01", server 2 will have "TextDoc02" in their shares). · Create a DFS name space. Add those shares to the name space. · On a domain joined endpoint, navigate to the DFS namespace you created. You should be able to see both files. · Create a DFS Replication group. Make it so that you have two way replication. You should now see both files on both servers. Make a change on one server and see if it replicates to another server. Does it work? Great. (you can shut down the file servers for now if you want or use them for the next step) · Configure WSUS so that you will only download Security updates for the desktop and server OS's ( highly recommend that you do not download any updates if you have access to the internet from this server) · Bonus points, install WSUS on another server and create a downstream server) · Create some groups in WSUS. Servers and endpoints will do nicely for names. · Create a new group policy that points workstations into the WSUS workstation group, points to WSUS for updates, and stop workstations from automatically downloading updates. · Read up on approving and pushing updates since the current assumption is that there are no updates to be pushed in this enclosed test network since there is no internet access to down load them. I believe there is a way to manually add updates to WSUS but I'm a bit foggy on that. Research it. · Do the same for servers. · Create a new AD user via powershell. · Create a new AD group via powershell. · Print a list of all domain users and computers in powershell, names only · Use powershell to pull a list of users who have remote as their office. If no users have remote listed as their office, use powershell to set that attribute and then pull users who have remote as their office. · Remove a user account from AD using powershell · Add a user to a group using powershell · Provision new AD users via a CSV in powershell This is really only scratching the surface of a
typical medium-large to enterprise level network. However, this should be
enough to get you started.
|
|
 0 Comments 0 CommentsTweet |



